A Comprehensive Guide to Performing a Crawl and Audit Scan on Burp Suite Professional: Identifying Vulnerabilities Effectively
7/2/20254 min read
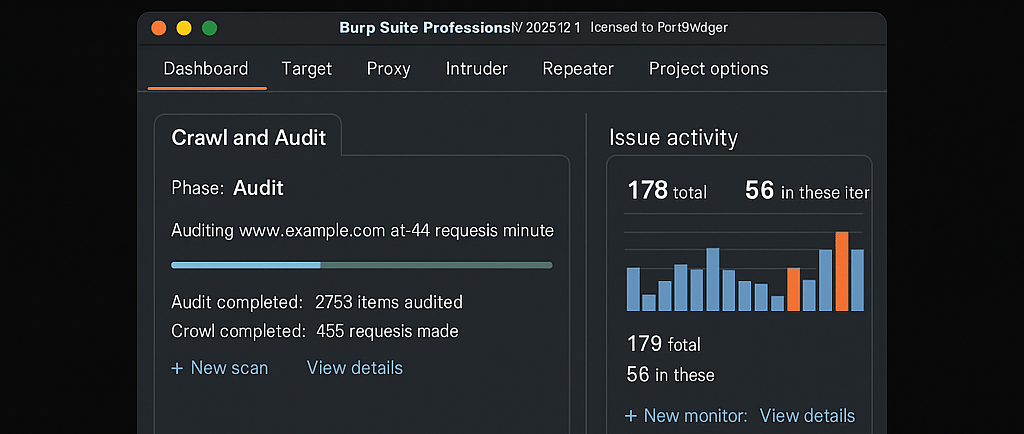

Introduction to Burp Suite Professional
Burp Suite Professional stands as a comprehensive and effective tool widely utilized for web application security testing. Developed by PortSwigger, it is designed to assist security professionals in identifying vulnerabilities within various web applications through a well-structured process. The suite integrates numerous features that facilitate an in-depth examination of web applications, making it an essential resource for cybersecurity experts.
One of the primary features of Burp Suite Professional is its crawler, which systematically navigates web applications to map out their structure and functionality. This intelligent crawling mechanism scans every page and element, allowing security testers to identify and analyze entry points for vulnerabilities. Additionally, the suite includes various tools for intercepting and modifying web traffic, thus providing professionals with the capability to evaluate how applications handle user input, a crucial aspect of vulnerability assessment.
Another notable aspect of Burp Suite is its robust scanning capabilities. The active and passive scan functionalities work in tandem to detect potential vulnerabilities such as SQL injection, cross-site scripting (XSS), and inadequate security controls. These automated processes streamline the auditing phase by providing timely insights into security gaps within the web applications, enabling teams to prioritize remediation efforts efficiently.
The importance of conducting crawl and audit scans cannot be overstated. In the rapidly evolving landscape of cybersecurity threats, web applications often become prime targets for exploitation. Regular assessments using tools such as Burp Suite are crucial in proactively identifying these vulnerabilities before they can be exploited by malicious actors. Thus, Burp Suite Professional not only aids in performing thorough assessments but also empowers organizations to fortify their web applications against potential attackers, making it a cornerstone in the arsenal of any security professional.
Setting Up Burp Suite for Crawling and Scanning
To effectively perform a crawl and audit scan using Burp Suite Professional, the initial setup is crucial. Start by downloading and installing the latest version of Burp Suite if you haven’t already done so. Once installed, open the application and navigate to the "Proxy" tab, which serves as the central hub for intercepting HTTP(S) traffic. Here, you will need to configure the proxy settings accordingly. By default, Burp listens to port 8080; however, this can be altered if your environment requires it. Ensure that your browser is set to use Burp's proxy address to facilitate the capture of requests.
Next, you will need to import the target web application into Burp Suite. To do this, navigate to the "Target" tab and add the specific URL of the application under "Site map." It’s also essential to define the scope of the crawl; this prevents Burp from scanning unintended external sites. Click on "Scope" and then include the target domain while ensuring that "Only in scope items" options are checked. This ensures a focused scanning process on your specified targets.
Furthermore, adjusting the scan settings is vital to optimize crawling. Under the "Scanner" settings, you can select various options such as “crawl depth” and “speed.” Opt for a moderate crawling depth initially, as this will allow for a comprehensive scan without overwhelming the application. Be cautious of setting the speed too high, as this can inadvertently trigger application firewalls or rate limiting mechanisms. Finally, consider enabling "Cookies" in Burp’s settings to ensure session handling is managed effectively. Common pitfalls during setup include misconfiguring proxy settings or neglecting to adjust scan settings appropriately, both of which could lead to incomplete data or false negatives during the scanning process.
Performing a Crawl and Audit Scan
To effectively utilize Burp Suite Professional for identifying vulnerabilities, it is essential to understand how to perform a crawl and audit scan. This process involves several systematic steps starting with the configuration of the tool to integrate it properly with your target application. First, ensure that the browser is set up to route traffic through Burp Suite, allowing the tool to intercept the requests made by the web application.
Once the setup is complete, initiate the crawling process by navigating to the desired URL within the browser. Burp Suite's crawling feature will automatically capture and explore the application, identifying various links and resources. During this phase, it is crucial to monitor the crawling progress in the ‘Target’ tab, where users can view the discovered sites as Burp Suite builds a comprehensive tree of the web application's structure.
After the crawl is finished, proceed to the audit scan. This can be accomplished by selecting the discovered URLs and selecting the ‘Scan’ option. Burp Suite will employ its robust scanning algorithms to search for common vulnerabilities such as XSS, SQL injection, and CSRF. As the scan progresses, the user can track its status in real time, which provides insights into the efficiency and areas being examined.
Upon completion of the audit scan, the results will be displayed in the ‘Scanner’ tab. This outcome includes detailed information on the vulnerabilities detected, ranked by severity. Prioritizing these vulnerabilities is critical; it enables security professionals to address high-risk issues first, ensuring a more effective remediation process. Users should focus on both the impact and exploitability of each vulnerability for an informed approach to enhancing their application security.
Analyzing and Reporting Vulnerabilities Discovered
Once the crawl and audit scan using Burp Suite Professional has been completed, the subsequent step involves a systematic analysis of the vulnerabilities that have been identified. This crucial phase not only allows for threats to be understood in context but also facilitates clear communication with stakeholders or clients. Effective documentation is essential in conveying the nature and severity of these vulnerabilities.
To begin with, it is imperative to categorize each vulnerability according to its risk level, typically ranging from low to critical. Many organizations utilize established grading systems such as the Common Vulnerability Scoring System (CVSS) to ensure standardized reporting. This assists in prioritizing remediation efforts, ensuring that more severe vulnerabilities are addressed promptly while also providing a clear framework for clients to understand the implications of the findings.
Additionally, best practices for documenting vulnerabilities include a detailed description of each issue, including the affected systems, potential impact, and evidence collected during the audit. Incorporating screenshots or logs from Burp Suite can enhance clarity, making it easier for technical teams to replicate issues. It is also beneficial to outline the recommended remediation strategies, providing actionable insights that can be readily implemented. These strategies might involve patching software, altering configurations, or implementing additional security controls to mitigate risk effectively.
Moreover, transparent communication of the findings to stakeholders is vital. This entails not only the delivery of a comprehensive report but also a potential follow-up meeting to discuss the findings and answer any questions. Ultimately, the goal is to ensure that vulnerabilities are not merely identified but addressed comprehensively, thereby enhancing the overall security posture of the web application. By following these guidelines, organizations can foster a proactive approach to security, ensuring that they effectively manage vulnerabilities uncovered during the audit process.
