Telstra Forage Job Simulation
I did the Job Sim for telson Cyber Security Analyst Task 3
Shubham Singla
11/14/2024


1. What was the task?
We needed to:
Simulate a firewall server that can filter malicious traffic.
Block malicious requests targeting a vulnerable endpoint (/tomcatwar.jsp) and exploit parameters (class.module.classLoader.resources.context.parent.pipeline).
Allow legitimate requests without disruption.
2. Understanding the setup
We used:
firewall_server.py: This Python script simulated the firewall server.
test_requests.py: A script to test the server by sending both malicious and legitimate requests.
3. Step-by-step process
Step 1: Create a basic server
We started with a simple server script (firewall_server.py) that could handle incoming HTTP requests. The server used Python’s http.server library to:
Accept GET and POST requests.
Print responses (allowed or blocked).
Here’s the original structure of the server:
from http.server import BaseHTTPRequestHandler, HTTPServer
host = "localhost"
port = 8000
class ServerHandler(BaseHTTPRequestHandler):
def do_GET(self):
self.send_response(200) # Always allow GET requests (initially)
def do_POST(self):
self.send_response(200) # Always allow POST requests (initially)
if name == "__main__":
server = HTTPServer((host, port), ServerHandler)
print("Server running...")
server.serve_forever()
Step 2: Add logic to filter malicious traffic
We modified the server to:
Block requests targeting /tomcatwar.jsp.
Block requests containing the malicious parameter class.module.classLoader.resources.context.parent.pipeline.
Here’s the updated server code:
from http.server import BaseHTTPRequestHandler, HTTPServer
from urllib.parse import urlparse, parse_qs
host = "localhost"
port = 8000
# Function to block malicious requests
def block_request(self):
self.send_response(403) # Forbidden response
self.end_headers()
self.wfile.write(b"Request Blocked")
# Function to allow legitimate requests
def allow_request(self):
self.send_response(200) # OK response
self.end_headers()
self.wfile.write(b"Request Allowed")
class ServerHandler(BaseHTTPRequestHandler):
def do_GET(self):
self.process_request()
def do_POST(self):
self.process_request()
def process_request(self):
# Parse the URL and query parameters
parsed_path = urlparse(self.path)
query_params = parse_qs(parsed_path.query)
# Read POST data (if any)
content_length = int(self.headers.get('Content-Length', 0))
post_data = self.rfile.read(content_length).decode('utf-8')
post_params = parse_qs(post_data)
# Block if malicious patterns are found
if (parsed_path.path == "/tomcatwar.jsp" or
"class.module.classLoader.resources.context.parent.pipeline" in query_params or
"class.module.classLoader.resources.context.parent.pipeline" in post_params):
block_request(self)
else:
allow_request(self)
if name == "__main__":
server = HTTPServer((host, port), ServerHandler)
print("[+] Firewall Server running on: %s:%s" % (host, port))
server.serve_forever()
Key Changes:
parsed_path.path == "/tomcatwar.jsp": Blocks requests to the malicious endpoint.
Check parameters:
Query parameters in GET requests: query_params.
POST parameters: post_params.
Step 3: Create a test script (test_requests.py)
This script simulated different types of requests to the server:
Malicious requests targeting /tomcatwar.jsp.
Malicious requests with exploit parameters.
Legitimate requests to safe paths.
Here’s the test script:
import requests
def test_firewall():
base_url = "http://localhost:8000"
test_cases = [
{"description": "Malicious request to /tomcatwar.jsp", "url": f"{base_url}/tomcatwar.jsp", "method": "GET", "expected_status": 403},
{"description": "Malicious request with exploit parameters", "url": f"{base_url}/safe_path", "method": "POST", "data": {"class.module.classLoader.resources.context.parent.pipeline": "exploit"}, "expected_status": 403},
{"description": "Legitimate request to /safe_path", "url": f"{base_url}/safe_path", "method": "GET", "expected_status": 200},
{"description": "Legitimate POST request to /safe_path", "url": f"{base_url}/safe_path", "method": "POST", "data": {"key": "value"}, "expected_status": 200},
{"description": "Another malicious request to /tomcatwar.jsp", "url": f"{base_url}/tomcatwar.jsp", "method": "POST", "expected_status": 403},
]
for i, test in enumerate(test_cases, 1):
print(f"Test {i}: {test['description']}")
try:
if test["method"] == "GET":
response = requests.get(test["url"])
elif test["method"] == "POST":
response = requests.post(test["url"], data=test.get("data", {}))
else:
print(f"Unsupported HTTP method: {test['method']}")
continue
print(f" - Expected: {test['expected_status']}, Got: {response.status_code}")
print(f" - {'PASS' if response.status_code == test['expected_status'] else 'FAIL'}\n")
except requests.exceptions.RequestException as e:
print(f" - Request failed: {e}\n")
if name == "__main__":
test_firewall()
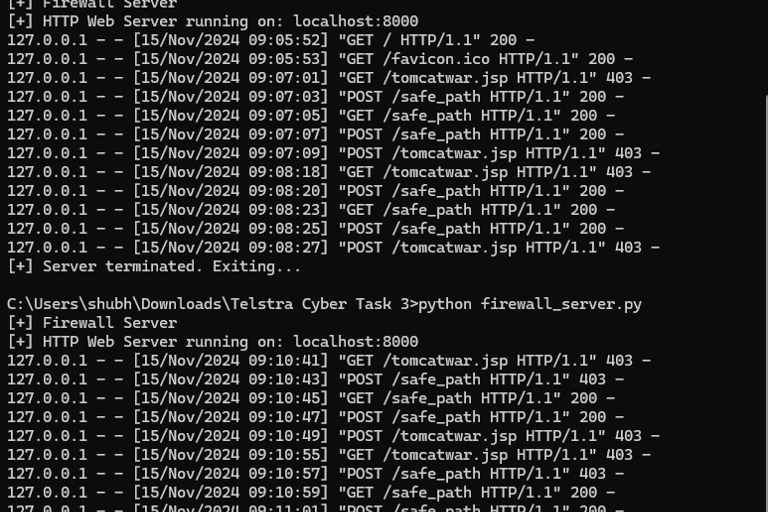
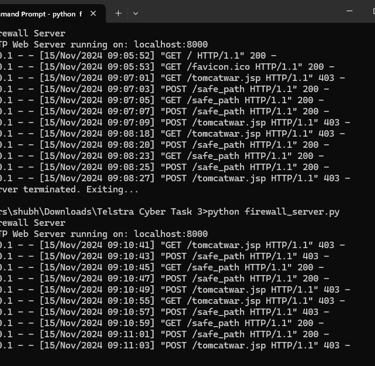
Step 4: Run and validate
Start the server:
cmd
Copy code
python firewall_server.py
Run the test script:
cmd
Copy code
python test_requests.py
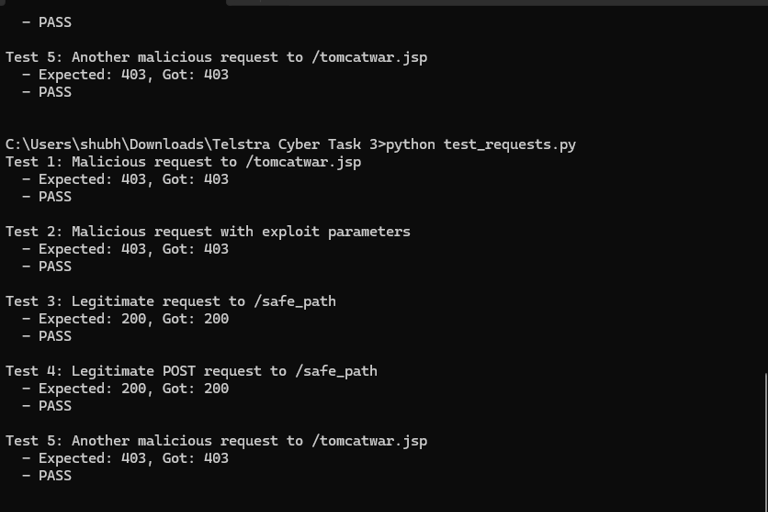
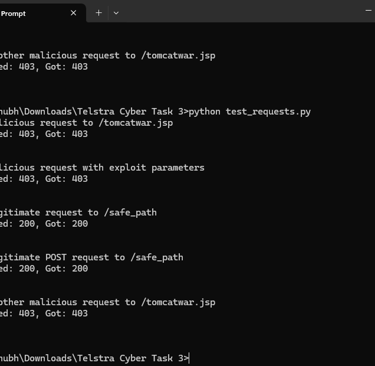
Results:
Malicious requests are blocked with 403.
Legitimate requests are allowed with 200.
Outcome
We successfully created a server that:
Blocks malicious requests to /tomcatwar.jsp or containing exploit parameters.
Allows legitimate traffic.
Contact me if you have any questions!