Zero Trust Architecture: The Future of Enterprise Security
In the face of increasingly sophisticated cyber threats, traditional "castle-and-moat" security models fall short. Enter Zero Trust Architecture (ZTA)—a cutting-edge cybersecurity approach built on the premise of "never trust, always verify."
Shubham Singla
11/27/20242 min read
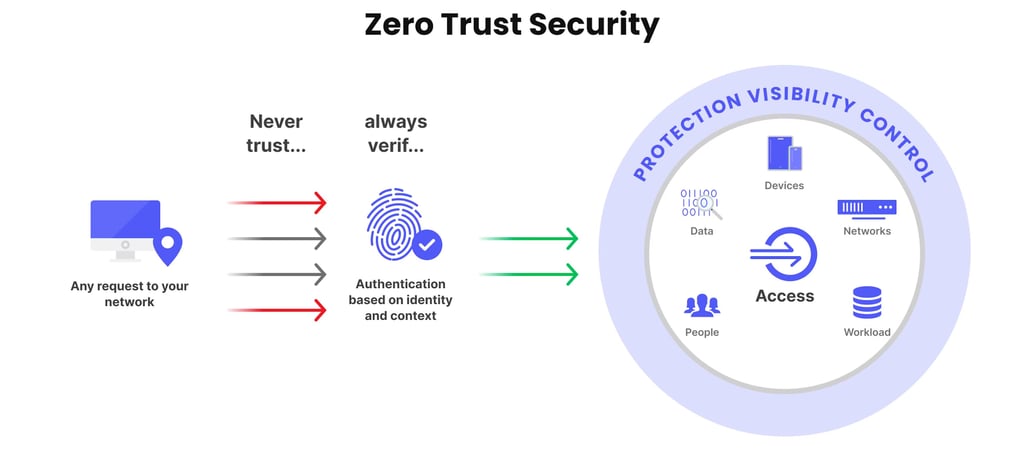
What is Zero Trust Architecture?
Zero Trust Architecture is a cybersecurity framework that enforces strict verification of every user and device attempting to access network resources, whether inside or outside the perimeter. This proactive approach minimises risk by assuming breaches are always possible.
Key Principles of Zero Trust
Verify Explicitly: Authenticate and authorise based on multifactor conditions such as identity, device, and location.
Use Least Privilege Access: Grant only the minimal permissions required to perform specific tasks.
Assume Breach: Design systems with the expectation of potential breaches, focusing on containment and response.
Why Zero Trust Matters
With the proliferation of cloud computing, remote work, and bring-your-own-device (BYOD) policies, traditional security boundaries no longer suffice. Zero Trust offers a dynamic, scalable solution for today’s security challenges.
Key Benefits
Reduced Attack Surface: Access is limited to what’s strictly necessary.
Enhanced Visibility: Real-time monitoring provides insights into user and device activity.
Streamlined Compliance: Simplifies adherence to GDPR, HIPAA, and other regulations.
How to Implement Zero Trust
Step 1: Map Critical Data and Workflows
Use tools like Varonis to identify and classify sensitive data, ensuring priority protection for high-value assets.
Step 2: Strengthen Identity and Access Management
Adopt tools such as Okta and Microsoft Azure Active Directory for secure authentication and single sign-on (SSO). Employ Multi-Factor Authentication (MFA) to add an extra layer of protection.
Step 3: Apply Network Segmentation
Leverage solutions like VMware NSX or Cisco Secure Workload for micro-segmentation, isolating sensitive resources from the broader network.
Step 4: Monitor Continuously with Advanced Tools
Utilise Palo Alto Cortex XDR or Splunk SIEM for real-time monitoring and incident detection. These tools provide actionable insights to detect and mitigate threats early.
Case Studies: Zero Trust in Action
Case Study 1: Google’s BeyondCorp
Google pioneered Zero Trust with its BeyondCorp initiative, moving away from perimeter-based security to authenticate users and devices at every access point.
Result: Seamless and secure remote access for a global workforce, enhancing both user experience and security.
Case Study 2: Healthcare Network Adopting Zero Trust
A large hospital network implemented Okta for identity management and Cisco Secure Workload for micro-segmentation to protect sensitive patient data.
Result: Achieved compliance with HIPAA regulations and reduced breach attempts to nearly zero over three years.
Case Study 3: Financial Institution's Cloud Transition
A financial institution leveraged Palo Alto Networks Prisma Access to secure customer data in its hybrid cloud environment. Micro-segmentation and continuous monitoring tools like Splunk enhanced overall resilience.
Result: Significant reduction in operational risks and enhanced customer trust.
Tools for Zero Trust Success
Here are some leading tools to consider when implementing Zero Trust:
Okta: Streamlines identity management and provides robust MFA capabilities.
Palo Alto Networks Prisma Access: Delivers secure remote access and advanced threat detection.
VMware NSX: Facilitates micro-segmentation to isolate sensitive resources.
Splunk SIEM: Offers real-time security monitoring and analytics.
Varonis: Protects critical data with automated classification and behaviour analytics.
Cisco Secure Workload: Simplifies workload segmentation to reduce lateral movement risks.
The Future of Cybersecurity is Zero Trust
Zero Trust is more than a buzzword—it’s a necessary shift in how organisations approach cybersecurity. With robust tools and strategic implementation, businesses can safeguard sensitive data, comply with regulations, and build customer trust.
Your journey to Zero Trust starts today. Equip your organisation with the tools and mindset to thrive in an increasingly connected world.
